Hello Chaos Podcast chats with Greg Hatcher

Jennifer Oladipo and Jennifer Sutton host Hello Chaos, a podcast that meets entrepreneurs at every point in their journey. It’s real talk about struggles and triumphs. White Knight Founder Gregory Hatcher had the opportunity to join them and discuss his founder journey and experience in network and web app penetration testing, red teaming, Python, and reverse engineering.
The Importance and Challenges of Cybersecurity Testing
In an article written by White Knight Labs cofounder Greg Hatcher and published in Government Technology Insider, Greg emphasizes the significance of cybersecurity testing for government agencies and companies to identify their vulnerabilities and improve their cybersecurity measures. The article mentions that cybersecurity partners vary in cost and expertise, and the greater risk an agency faces, the more intricate its testing will need to be, and the more experience its cybersecurity team will need. The article also highlights two types of cybersecurity testing: penetration testing and advanced adversarial emulation. The article also includes discussion of cybersecurity testing, vulnerabilities, and advanced adversarial emulation.
Unveiling OSINT Techniques: Exploring LinkedIn, Illicit Services, and Dehashed for Information Gathering
Introduction Open Source Intelligence (OSINT) is becoming increasingly popular due to its effectiveness in gathering information. The purpose of this blog is to explore the use of LinkedIn, Illicit Services, and Dehashed for OSINT purposes. This blog will also discuss ethical and legal considerations for using these techniques I. Identifying a Company for the Proof of Concept (POC) For the purpose of this blog, Ronin Innovations Group was chosen as the company to demonstrate the effectiveness of OSINT techniques. Ronin Innovations Group is a rapidly growing technology company that specializes in developing innovative solutions for various industries, including healthcare, finance, and telecommunications. The company has a global presence, with operations in multiple countries, and is known for its commitment to research and development to stay ahead of the competition. With its focus on cutting-edge technology and solutions, Ronin Innovations Group is an ideal target for OSINT investigations to gather information on key personnel, company strategies, and potential vulnerabilities. II. Gathering Information from LinkedIn A. Utilizing Search Filters and Advanced Techniques LinkedIn is an essential tool for gathering information about the employees of a company. Using LinkedIn search filters can help identify specific industries and job titles. Advanced search techniques can also be used to find relevant information. Results of LinkedIn Scraping To scrape employee data from LinkedIn, the LinkedInDumper tool was used. The program was able to identify over 1,000 active Ronin Innovations Group employees on LinkedIn. However, due to the limitations of the LinkedInDumper tool, it was only able to export 65 employee accounts. This was because LinkedIn restricts the number of search results to the first 1,000, and not all employee profiles may be public, making it difficult to extract the first name, last name, and profile URL of some employee accounts. The LinkedInDumper tool only displays public profiles, and those that are private or have default values such as “LinkedIn” as the first name and “Member” as the last name are not included. Additionally, some LinkedIn users may name their profile using various salutations, abbreviations, emojis, and middle names, which may be challenging to filter out. It is essential to note that the LinkedInDumper tool relies on an unofficial API called Voyager and is not using the official LinkedIn API, which may also contribute to limitations in data extraction. III. Exploring Illicit Services Illicit Services are services available on the dark web that can be used for gathering personal and sensitive information. These services are accessible for free and can include services such as password cracking and phone number reverse lookup. These services can be used to find leaked credentials and other sensitive information obtained through data breaches. A. Risks and Legal Implications Utilizing the service Illicit Services for OSINT purposes can expose an individual to legal and personal risks. The use of these services can violate various laws and regulations, including data privacy laws and intellectual property laws. It is crucial to consider the legal implications of accessing such services before using them for OSINT investigations. Furthermore, using these services can also result in personal risks, including the exposure of sensitive information or becoming a victim of cybercrime. It is important to exercise caution and use these services only for lawful and ethical purposes. B. Results of OSINT with Illicit Services By utilizing the Illicit-Services-Enum-Script, a custom script created by White Knight Labs, we were able to conduct the enumeration of accounts based on our search criteria, resulting in the initial identification of 40 accounts. However, through a meticulous manual examination of the gathered data, we were able to validate an additional 14 employee accounts that were still active at Ronin Innovations Group. These newly discovered accounts have been seamlessly integrated into the LinkedInDumper results, resulting in a total of 79 identified accounts that perfectly met the objectives of our OSINT research. During the OSINT investigation of Ronin Innovations Group, extensive personal information was uncovered on employee Haley. Her LinkedIn profile provided details on her employment, gender, location, inferred salary, and various social media usernames and contact information. Further research revealed additional information, including her attendance at the University of Toledo and her Twitter username. In addition, an online search uncovered Haley’s address and vehicle information, including the make, model, and VIN number. The investigation also yielded some information on employees Drew and Diana, including their contact information and employment details at Ronin Innovations Group. While utilizing Illicit Services for OSINT investigations can provide valuable data, it is crucial to consider the risks and legal implications associated with accessing such services. It is important to exercise caution and use these services only for lawful and ethical purposes. IV. Leveraging Dehashed for OSINT Investigations A. Introduction to Dehashed Dehashed is a paid data breach search engine that can be used to find leaked credentials and other sensitive information. For this investigation, a combination of two tools were used, specifically, the Dehashed Query and Crack and the dehashQuery tool. B. Benefits and Limitations Using Dehashed for OSINT investigations can provide valuable data, including leaked credentials and sensitive information. However, it is crucial to consider the accuracy and completeness of the information obtained. It is also important to note that Dehashed is a paid service and requires a subscription to access all features. C. Results of Dehashed Investigation The results obtained from Dehashed for the Ronin Innovations Group investigation included 14 cracked hashes and 20 uncracked hashes, but these were not relevant to the investigation as they were associated with ex-employees. However, Dehashed provided additional value by allowing us to reverse a phone number that was collected from Illicit Services for Diana. This helped us confirm the phone number’s match and current address. V. Combining Techniques and Analyzing the Gathered Information A. Applying Techniques to the Chosen Target To effectively gather information about potential targets for a phishing campaign, it is crucial to apply the techniques discussed in the blog. In this case, the chosen target is Ronin Innovations Group. The following information was obtained using OSINT techniques:
Cobalt Strike may be a double-edged sword but pentesting tools are invaluable, says expert
In the article by Damien Black and posted on CyberNews, Greg Hatcher, co-founder of White Knight Labs, discusses the growing concern surrounding the use of Cobalt Strike, a widely recognized penetration testing tool, by cybercriminals for malicious activities. The article highlights the challenges in stopping malware created with Cobalt Strike and explores the potential implications of advancements in artificial intelligence and machine learning on malware development. Hatcher also mentions other dual-use tools like BloodHound and Burp Suite, which can be utilized by both attackers and defenders in the cybersecurity realm. He emphasizes the significance of strong cybersecurity practices, such as implementing multifactor authentication and keeping operating systems updated, to prevent cyberattacks. Furthermore, the article cautions that cybercriminals are increasingly incorporating code from pentesting tools into their custom malware, underlining the need for constant vigilance within the cybersecurity industry. Read full article
How to prevent deepfakes in the era of generative AI
An article by George Lawton published on TechTarget discusses the growing threat of deepfake attacks in the era of generative AI and provides recommendations for preventing and detecting them, featuring insights from Greg Hatcher, co-founder of White Knight Labs. The article highlights the importance of developing strong security procedures, including multistep authentication processes, and staying up to date on the latest tools and technologies to thwart increasingly sophisticated deepfakes. Greg Hatcher emphasizes the telltale signs of audio deepfakes, such as choppy sentences, unusual word choices, and abnormal inflection or tone of voice, and the use of forensic analysis and specialized software for reverse image searches to detect manipulation or alteration. The article cites examples of deepfake attacks, including a $243,000 bank transfer resulting from a phone request impersonation and a $35 million fraudulent bank transfer timed perfectly with a company acquisition. The article also warns of the likely proliferation of deepfakes as a service and the need for collaboration between the public and private sectors to promote truth in social engagement. By staying vigilant and informed, businesses and individuals can better protect themselves against the deceptive power of deepfakes in this rapidly advancing era of generative AI. Read article
Why CFOs Need to Evaluate and Prioritize Cybersecurity Initiatives
In a post on Rush Hour Times, the author emphasizes the crucial role cybersecurity plays for CFOs and C-suite members. Greg Hatcher, CEO of White Knight Labs, highlights the risks of cyber threats and their potential impact on financial performance, reputation, and customer trust. The article provides recommendations for CFOs to prioritize cybersecurity investments and ensure compliance with data protection regulations. These recommendations include conducting regular security training, implementing access controls, monitoring employee activities, and performing comprehensive risk assessments to identify potential threats and vulnerabilities. Hatcher also stresses the importance of cloud provider security protocols and compliance requirements, as well as the need for employee training on securely accessing and managing cloud data. Finally, the article discusses the cybersecurity risks associated with remote and hybrid working policies, and provides recommendations for minimizing these risks, such as implementing multi-factor authentication and endpoint protection, and setting up VPNs to automatically disconnect when not in use.
You’re likely to see more robot security guards
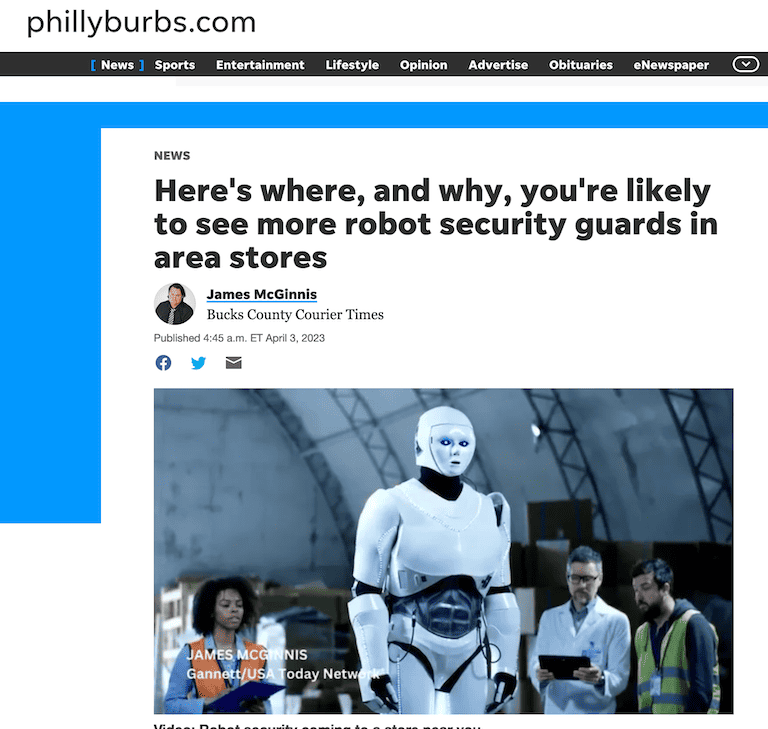
An article written by James McGinnis of the Bucks County Courier Times discusses the increasing use of robot security guards in various public spaces, including stores, casinos, college campuses, and hospitals. The robots, designed to record 360-degree HD video, detect thermal anomalies, and scan license plates, are already being used by companies such as Lowe’s and Knightscope. While some experts predict that robots will eventually replace some human labor, others argue that robots will provide companies with much more than security, such as collecting consumer data on “pattern of life” for companies seeking to sell products. However, the article also raises concerns about the use of robots and the data collected by them, as well as the need for humans to become more comfortable with the machines. White Knight Labs CEO Greg Hatcher is quoted in the article. read Article
White Knight Labs Is a Go-To Cyber Consultancy
An article by Amit Chowdhry posted on Pulse 2.0 discusses White Knight Labs, a cybersecurity consultancy founded by Greg Hatcher and John Stigerwalt, specializes in penetration testing and red teaming. The company focuses on providing deep technical expertise at a reasonable price, and its team of engineers have a wide range of specialties, such as Windows implant development and iOS application testing. White Knight Labs is currently working on a web application for red teamers to automate Endpoint Detection and Response (EDR) bypass features, as well as creating an OnDemand offering of their Offensive Development and Advanced Red Team Operations courses. read article
Revolutionizing Cybersecurity with GPT
This article, written by Greg Hatcher, CEO of White Knight Labs, discusses how the generative pre-trained transformer (GPT) can be used as a powerful tool for cybersecurity. GPT is a type of artificial intelligence that uses machine learning to process natural language. The article explains how GPT can be used to improve all facets of cybersecurity strategies, including threat detection, password analysis, and social engineering attack detection. However, the article also warns that GPT can be used by threat actors to carry out more effective attacks, and that cybersecurity professionals need to stay ahead of those who seek to use the same capabilities of GPT to undermine security. Overall, the article highlights the potential benefits and risks of using GPT in cybersecurity and emphasizes the importance of properly guarding GPT systems to prevent malicious attacks. Read article by Greg Hatcher