Introduction
Open Source Intelligence (OSINT) is becoming increasingly popular due to its effectiveness in gathering information. The purpose of this blog is to explore the use of LinkedIn, Illicit Services, and Dehashed for OSINT purposes. This blog will also discuss ethical and legal considerations for using these techniques
I. Identifying a Company for the Proof of Concept (POC)
For the purpose of this blog, Ronin Innovations Group was chosen as the company to demonstrate the effectiveness of OSINT techniques. Ronin Innovations Group is a rapidly growing technology company that specializes in developing innovative solutions for various industries, including healthcare, finance, and telecommunications. The company has a global presence, with operations in multiple countries, and is known for its commitment to research and development to stay ahead of the competition. With its focus on cutting-edge technology and solutions, Ronin Innovations Group is an ideal target for OSINT investigations to gather information on key personnel, company strategies, and potential vulnerabilities.
II. Gathering Information from LinkedIn

A. Utilizing Search Filters and Advanced Techniques
LinkedIn is an essential tool for gathering information about the employees of a company. Using LinkedIn search filters can help identify specific industries and job titles. Advanced search techniques can also be used to find relevant information.
Results of LinkedIn Scraping
To scrape employee data from LinkedIn, the LinkedInDumper tool was used. The program was able to identify over 1,000 active Ronin Innovations Group employees on LinkedIn. However, due to the limitations of the LinkedInDumper tool, it was only able to export 65 employee accounts. This was because LinkedIn restricts the number of search results to the first 1,000, and not all employee profiles may be public, making it difficult to extract the first name, last name, and profile URL of some employee accounts. The LinkedInDumper tool only displays public profiles, and those that are private or have default values such as “LinkedIn” as the first name and “Member” as the last name are not included. Additionally, some LinkedIn users may name their profile using various salutations, abbreviations, emojis, and middle names, which may be challenging to filter out. It is essential to note that the LinkedInDumper tool relies on an unofficial API called Voyager and is not using the official LinkedIn API, which may also contribute to limitations in data extraction.

III. Exploring Illicit Services
Illicit Services are services available on the dark web that can be used for gathering personal and sensitive information. These services are accessible for free and can include services such as password cracking and phone number reverse lookup. These services can be used to find leaked credentials and other sensitive information obtained through data breaches.
A. Risks and Legal Implications
Utilizing the service Illicit Services for OSINT purposes can expose an individual to legal and personal risks. The use of these services can violate various laws and regulations, including data privacy laws and intellectual property laws. It is crucial to consider the legal implications of accessing such services before using them for OSINT investigations.
Furthermore, using these services can also result in personal risks, including the exposure of sensitive information or becoming a victim of cybercrime. It is important to exercise caution and use these services only for lawful and ethical purposes.
B. Results of OSINT with Illicit Services
By utilizing the Illicit-Services-Enum-Script, a custom script created by White Knight Labs, we were able to conduct the enumeration of accounts based on our search criteria, resulting in the initial identification of 40 accounts. However, through a meticulous manual examination of the gathered data, we were able to validate an additional 14 employee accounts that were still active at Ronin Innovations Group. These newly discovered accounts have been seamlessly integrated into the LinkedInDumper results, resulting in a total of 79 identified accounts that perfectly met the objectives of our OSINT research.
python3 illicit-services.py --email test@RoninInnovationsGroup.org --max-request --email_domain RoninInnovationsGroup.org
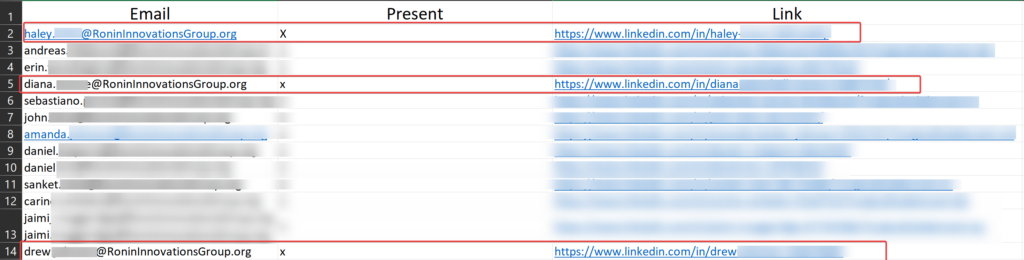
During the OSINT investigation of Ronin Innovations Group, extensive personal information was uncovered on employee Haley. Her LinkedIn profile provided details on her employment, gender, location, inferred salary, and various social media usernames and contact information. Further research revealed additional information, including her attendance at the University of Toledo and her Twitter username. In addition, an online search uncovered Haley’s address and vehicle information, including the make, model, and VIN number. The investigation also yielded some information on employees Drew and Diana, including their contact information and employment details at Ronin Innovations Group.
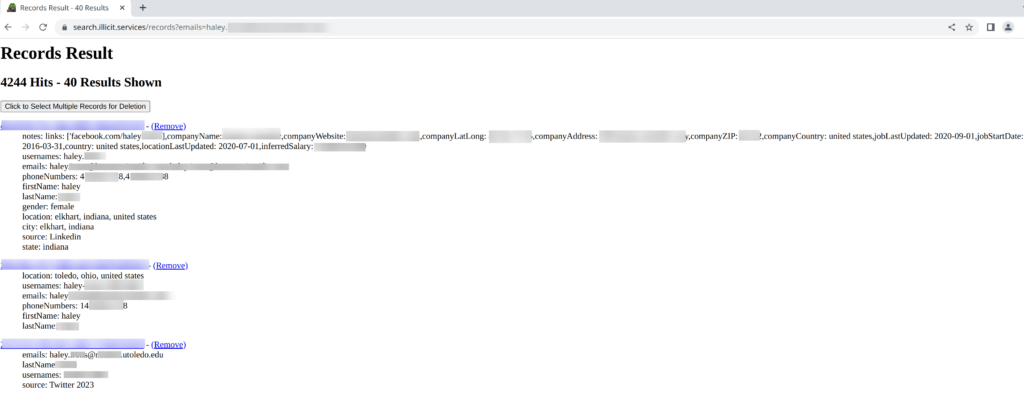
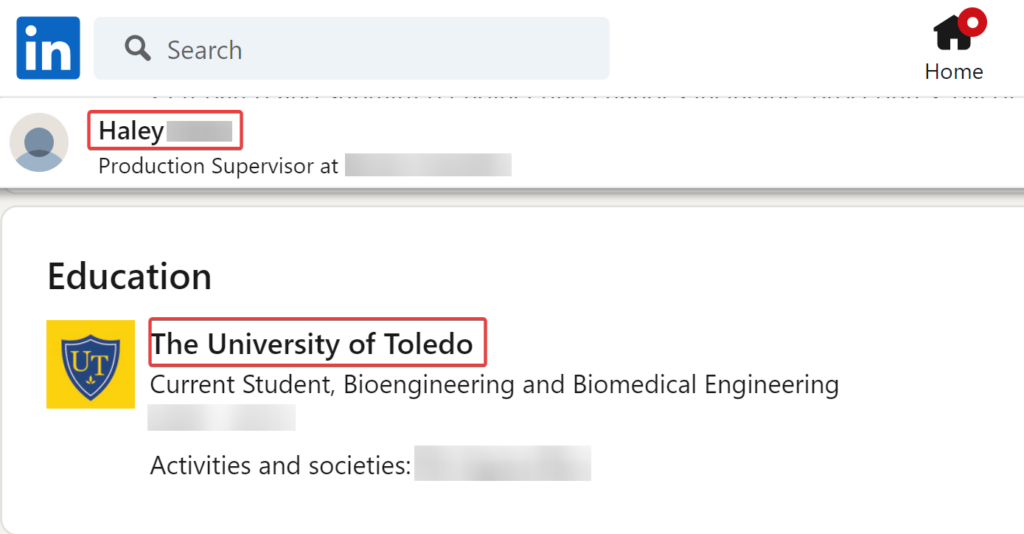
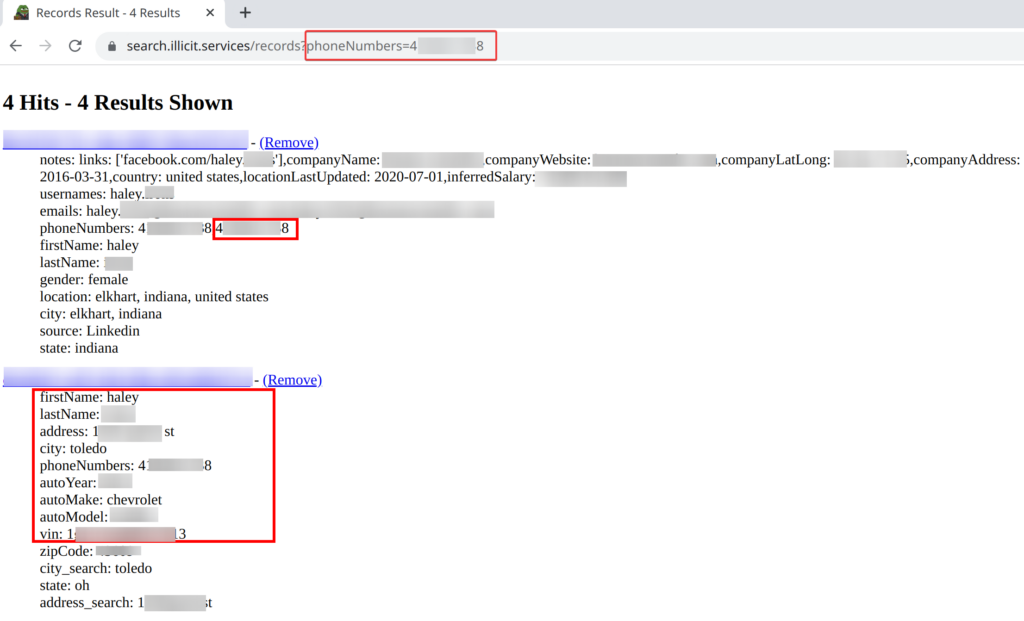
While utilizing Illicit Services for OSINT investigations can provide valuable data, it is crucial to consider the risks and legal implications associated with accessing such services. It is important to exercise caution and use these services only for lawful and ethical purposes.
IV. Leveraging Dehashed for OSINT Investigations
A. Introduction to Dehashed
Dehashed is a paid data breach search engine that can be used to find leaked credentials and other sensitive information. For this investigation, a combination of two tools were used, specifically, the Dehashed Query and Crack and the dehashQuery tool.
B. Benefits and Limitations
Using Dehashed for OSINT investigations can provide valuable data, including leaked credentials and sensitive information. However, it is crucial to consider the accuracy and completeness of the information obtained. It is also important to note that Dehashed is a paid service and requires a subscription to access all features.
C. Results of Dehashed Investigation
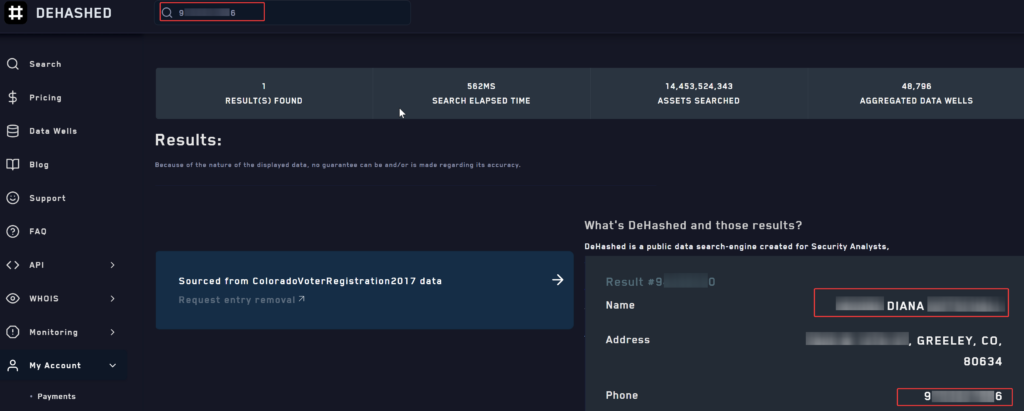
The results obtained from Dehashed for the Ronin Innovations Group investigation included 14 cracked hashes and 20 uncracked hashes, but these were not relevant to the investigation as they were associated with ex-employees. However, Dehashed provided additional value by allowing us to reverse a phone number that was collected from Illicit Services for Diana. This helped us confirm the phone number’s match and current address.
V. Combining Techniques and Analyzing the Gathered Information
A. Applying Techniques to the Chosen Target
To effectively gather information about potential targets for a phishing campaign, it is crucial to apply the techniques discussed in the blog. In this case, the chosen target is Ronin Innovations Group. The following information was obtained using OSINT techniques:
- 79 active employees identified on LinkedIn using the LinkedInDumper tool, including their usernames on Facebook and LinkedIn, email addresses, phone numbers, locations, inferred salaries, and employment details at Ronin Innovations Group.
- The LinkedIn profiles of three specific employees at Ronin Innovations Group: Drew, Haley, and Diana. The profiles provided additional details such as their gender, inferred salaries, and inferred employment details at Ronin Innovations Group. Additional information was obtained about their locations, education, and Twitter usernames.
- Results from Dehashed investigation provided additional value by allowing us to reverse a phone number that was collected from Illicit Services for Diana, helping us confirm the phone number’s match and current address.
By combining and analyzing this information, an attacker could potentially create a big list of potential users to target for a phishing campaign. Based on the hierarchical structure of Ronin Innovations Group, it would be strategic to target employees in higher positions such as managers or executives as they may have more access to sensitive information. Additionally, targeting employees in departments such as finance or human resources could potentially yield valuable information.
With the information obtained from OSINT techniques, an attacker could personalize their phishing campaign by using the information to craft a convincing and targeted message. This approach could significantly increase the chances of the attack being successful, highlighting the importance of ethical considerations and the need for consent when conducting OSINT investigations.
Countermeasures and Defense Strategies
Companies and individuals can take several steps to protect themselves from OSINT-based attacks:
- Strengthen privacy settings: Configure privacy settings on social media accounts and other online platforms to limit the exposure of personal and sensitive information.
- Educate employees: Conduct regular training sessions to educate employees about phishing attempts, social engineering tactics, and the importance of protecting sensitive information.
- Implement a robust cybersecurity policy: Develop and enforce a comprehensive cybersecurity policy that includes guidelines on password management, access control, and data protection.
- Monitor online presence: Regularly monitor your online presence to identify and address potential vulnerabilities, such as exposed sensitive data or unauthorized access to accounts.
Conclusion
In conclusion, using LinkedIn, Illicit Services, and Dehashed for OSINT investigations can provide valuable data that can be used in various scenarios, including threat intelligence, due diligence, and investigations. However, ethical and legal considerations must be taken into account when conducting these investigations. These techniques should be used responsibly and with the utmost care. Before conducting OSINT investigations, it is crucial to research and understand the applicable laws and regulations in the target jurisdiction. Additionally, individuals and companies must obtain proper consent when necessary, and they should not use these techniques for malicious purposes.
White Knight Labs
OSINT Services
White Knight Labs offers advanced Open Source Intelligence (OSINT) investigations conducted by our highly skilled team members who are trained in intelligence collection, analysis, and exploitation techniques. Our OSINT investigations are included as a standard part of our external pentest services and are hardcoded into our testing methodologies. We also provide a follow-up service in Industrial Espionage and Insider Threat training for corporations for any concerning issues identified during the OSINT investigation. Our mission is to equip companies and individuals with the necessary tools, knowledge, and resources to enhance their cybersecurity posture and protect themselves against OSINT-based attacks.


