I was recently browsing a large online retailer and came across this headline for a product:
BOBLOV KJ21 Body Camera, 1296P Body Wearable Camera Support Memory Expand Max 128G 8-10Hours Recording Police Body Camera Lightweight and Portable Easy to Operate Clear Night Vision … (emphasis added)
As a former police officer, now a security researcher with a keen interest in IoT targets, I was intrigued by “Boblov” – a name I had never encountered. I conducted some open-source intelligence (OSINT) research. I discovered from multiple sources, including the UK’s Intellectual Property Office and Boblov’s “About Us” page, that Boblov seems to be a brand under Shenzhen Lvyouyou Technology Co. Ltd. However, a preliminary search yielded little information about Shenzhen Lvyouyou Technology Co. Ltd.
The Boblov brand has a website at Boblov.com, which as of this writing, the domain register was listed as “Alibaba Cloud Computing (Beijing) Co., Ltd.”
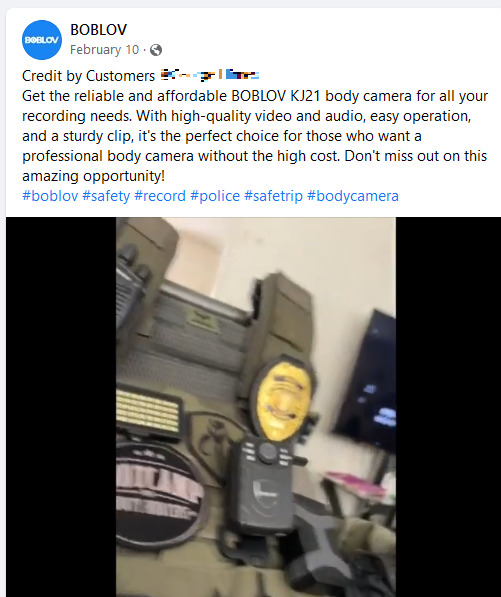
Boblov’s product page for the KJ21, and their Facebook page (BOBLOVGlobal), openly advertise their range of products as “Police” body cameras. A particular Facebook post (left image, click for larger view) showcases the KJ21, accompanied by hashtags “police” and “bodycamera.” On initial viewing, the imagery might strike someone as somewhat “tactical” or “law enforcement” oriented. However, upon closer examination of the video, it became evident that there was something off about this impression. By pausing and zooming in on the footage, it became clear that the person featured wasn’t law enforcement but a private Bail Bonds agent, often colloquially known as a “bounty hunter.”
While such agents provide an essential service for the companies they work for, they are not “police” or state agents.
In another striking example of Boblov seemingly failing to comprehend the market they are presumably targeting, this Facebook post (right image, click for larger view), at a superficial glance, might seem to feature someone who could pass for an official.
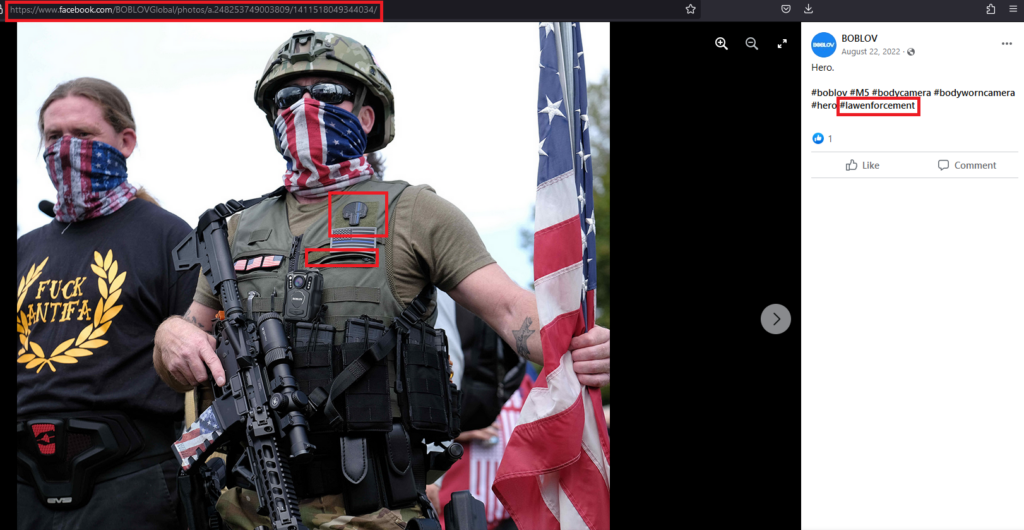
However, the absence of identifiers such as a badge, name tag, and patches, along with the context of the photo, clearly indicates that this individual is not operating in an official law enforcement capacity. Nevertheless, Boblov’s caption of “Hero” coupled with the hashtag “#lawenforcement” comes across as perplexing.
By this point, I had discovered that Boblov, a brand owned by a Chinese entity with no significant online presence, was advertising “Police Body Cameras.” However, their marketing team seemed to struggle to locate actual law enforcement officers to demonstrate their product. Alternatively, it appeared that this company, which marketed and sold “law enforcement” products in the US, did not fully comprehend the definition and composition of law enforcement.
As I dug further, I came across a customer asking for help because they could not reset their password to get into their device. Boblov’s answer: “We could send you the universal password….”

Click for larger
Excellent. I’m sold. I got myself a KJ21. Let the fun begin.
Assessment Purpose and Conditions
The security and risk assessment on the Boblov KJ21, referred to hereafter as “the target,” was a “black box” examination. The only information used was that which could be obtained through open sources. This risk and security assessment aims to produce a structured qualitative evaluation of the target that can assist others in making informed decisions about risk. Notably, due to pre-engagement research that repeatedly suggested that the target is suitable for law enforcement use or is already employed in a security or law enforcement setting, the adopted information security standards and controls are reflective of this operational environment.
Various tables at the end of this report provide further definitions and context.
Scope
The scope of the assessment assessed the effectiveness of the target’s controls to eliminate or mitigate external or internal threats from exploiting vulnerabilities. Should the target’s control fail, the result could be:
- Unauthorized disclosure of data
- Unauthorized modification to the system, its data, or both
Boblov KJ21: Target Information
The Boblov K21 (“the target”) is a compact device with a rounded rectangular shape, measuring 2.95 x 2.17 x 0.98 inches and weighing approximately 14.5 ounces. The target has a USB port and a TransFlash (TF) Card slot for connectivity and storage.
The camera is on the “front” side of the device, while the “rear” side features an LCD screen. Below the screen are four control buttons for reviewing video and audio content, viewing pictures, and adjusting settings. In addition, a reset button is tucked away, accessible with a small paperclip or similar pin-like objects.
The device is held together by four screws – two on the front and two on the back – hidden beneath easily removable rubber plugs. You can use an unfolded paperclip to dislodge these plugs. Although a precision screwdriver kit would be handy for unscrewing, once the screws are out, the KJ21 can be conveniently opened. The following items were identified on the circuit board:
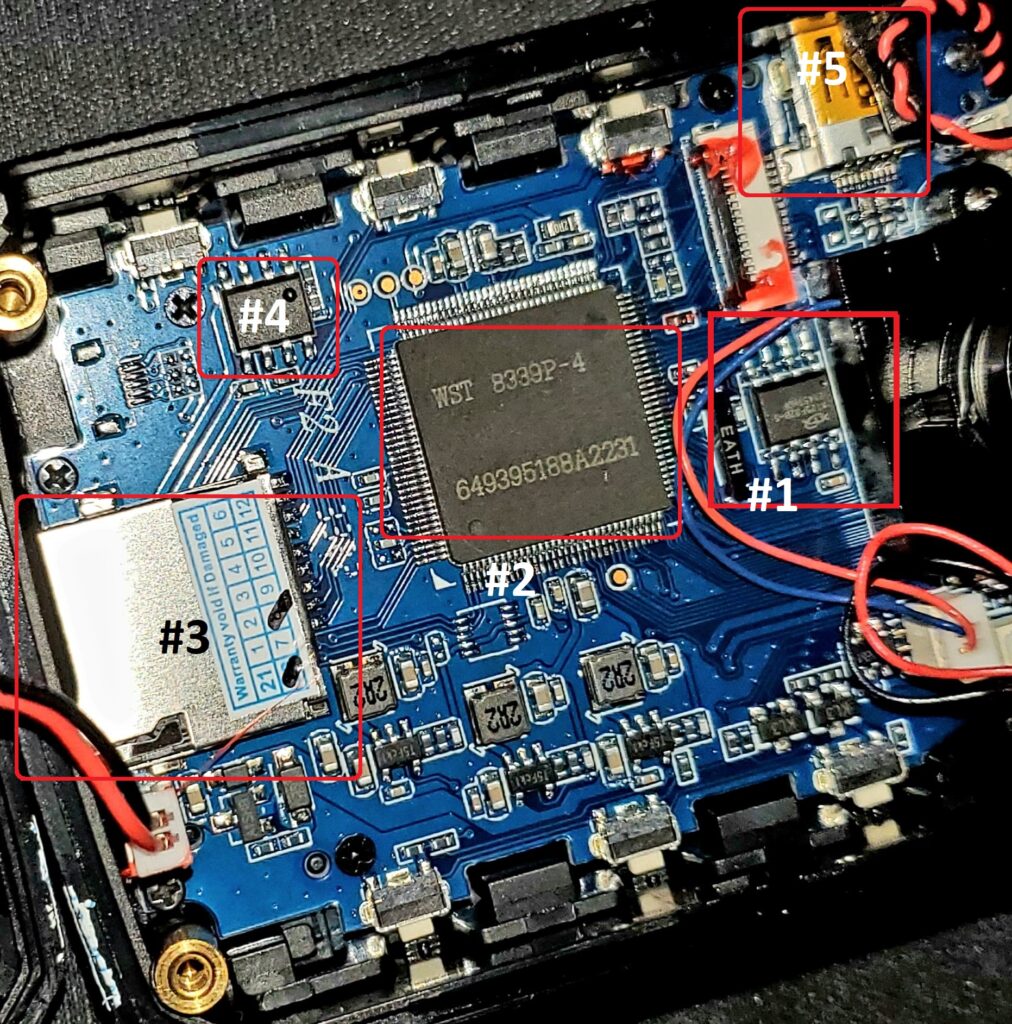
#1 XT25F32B-S Quad IO Serial NOR Flash
#2 WST 8339P-4 649395188A2231
#3 TF Card Housing
#4 ETA40543 A283I (1.2A/16V Fully Integrated Linear Charger for 1 Cell 4.35V Li-ion Battery)
#5 USB Input
Click for larger
XT25F32B-S Quad IO Serial NOR Flash
As of this writing, the current version 1.3 of flashrom does not support the XT25F32B. Using the datasheet, I managed to customize flashrom and get it working. I provide the code you can add to the flashrom source and rebuild if desired. Though the contents could ultimately be dumped, this ultimately proved unnecessary.

Click for larger
TF Card Storage
The target formats the TF Card using FAT32. At the root level, there are three main objects:
- DCIM: folder with recorded video, audio, and photos, each in sub-folders.
- LOG: folder which contains day-separated text files of target events, such as when the target was plugged into the USB, turned off, the picture was taken, and more.
- Param.ini: a file whose only purpose seems to mark the card as belonging to a particular device. Either way, it contains the user-assigned Device ID and the assigned “Officer ID.”
The TF Card is not encrypted when the device password is set and enabled. Because of this, removing the card and mounting it as just a regular TF Card allows full control of the card’s contents.
Device Password
By default, the target’s password is disabled. When enabled, the default password is 000000. The operator can change the target’s password to any 0-9A-Z string that is six characters long.
The effect of setting a password:
- Password is required to make certain changes, such as formatting the TF card.
- Password is required for the target to mount the TF card when connected to a computer via a USB cable.
During the assessment, the “universal” password was discovered to be: 888888
Target USB Computer Connection
When the target is connected to a desktop computer, the target checks to see if the password is enabled; if not, the TF Card is presented as a drive to the operating system, and the TF Card’s contents, including the logs, video, photos, and audio can be read.
If the target has a password set, the user must first enter the password on the target, and then the TF Card is presented as a drive.
In either case, regular users only have read access to contents. However, users with administrative/root privileges do have the ability to edit content.
The “universal” password (888888) unlocks the device regardless of the password.
Log Modification
Because the main storage (the TF Card) is easily removable, and even if it were “super-glued” in, the “universal” password makes achieving access via USB trivial, the integrity of logs was put to the test.
It was discovered that modifying and deleting logs without apparent alarm or issue was possible. Once modified or removed, the target continued to function without apparent issue, no further alarm or warning was given or other log entries made.
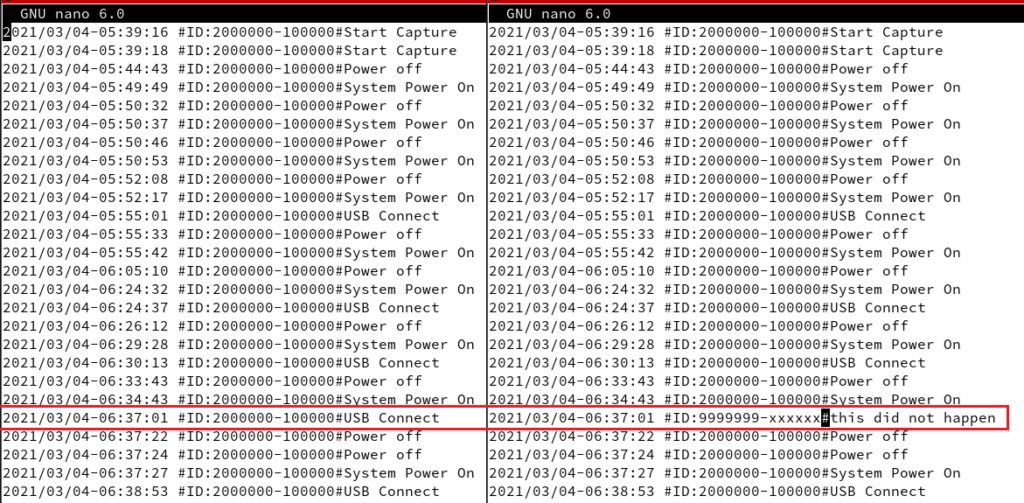
Click for larger
Recording Manipulation
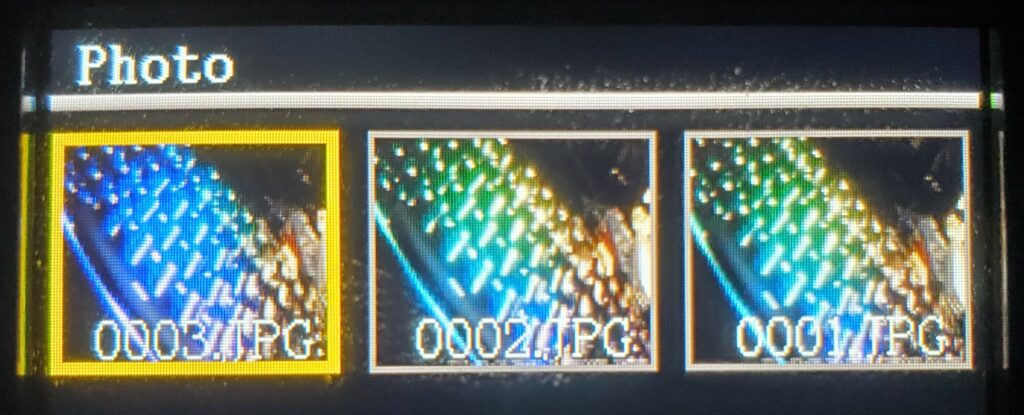
The same lack of integrity control was also observed for recorded media. I could delete, edit, or modify recorded media, at will, without apparent alarm. In these images, I even demonstrate how it is possible to make an entire recorded event “disappear” like it never happened, including removing the entry from the logs and aligning the filename scheme so there is no gap.
Mounted, we see the three files here (note the last three digits match the numbers from the above image).

Click the image for a larger view
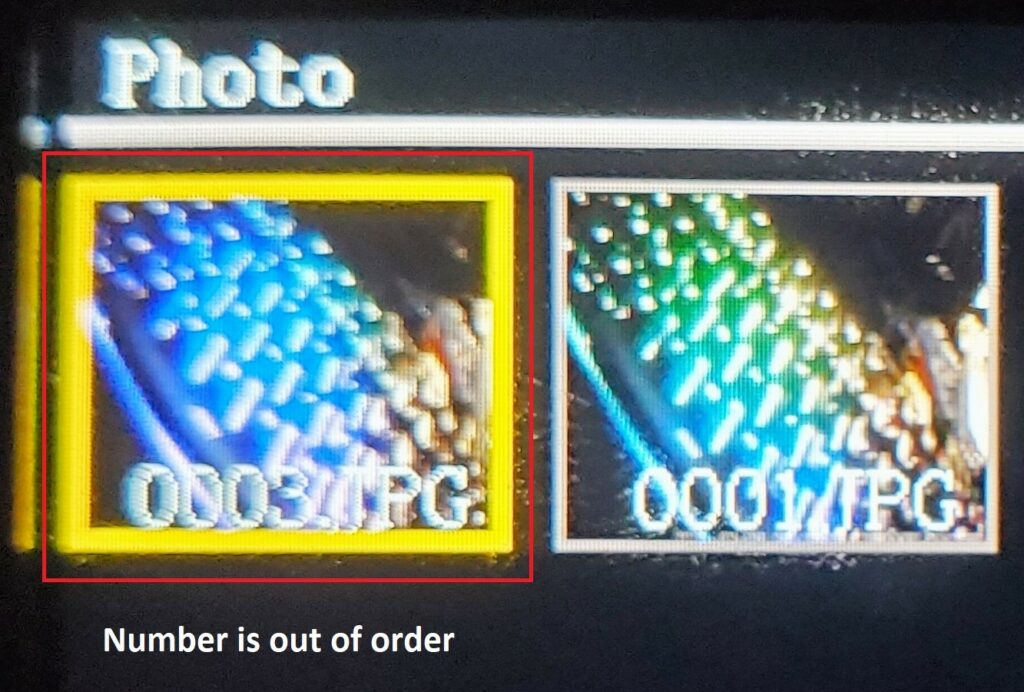
Once mounted, sure, we could delete the file. However, Two problems arise. First, the sequence numbers 001, 002, and 003 could get out of wack (as the image to the left shows). Second, the log entry will still show a photograph was taken. Thankfully we have a “universal” password and root access to the TF Card.
We need to edit the log and delete the files. The image below shows the log entry and the corresponding image that must be deleted.
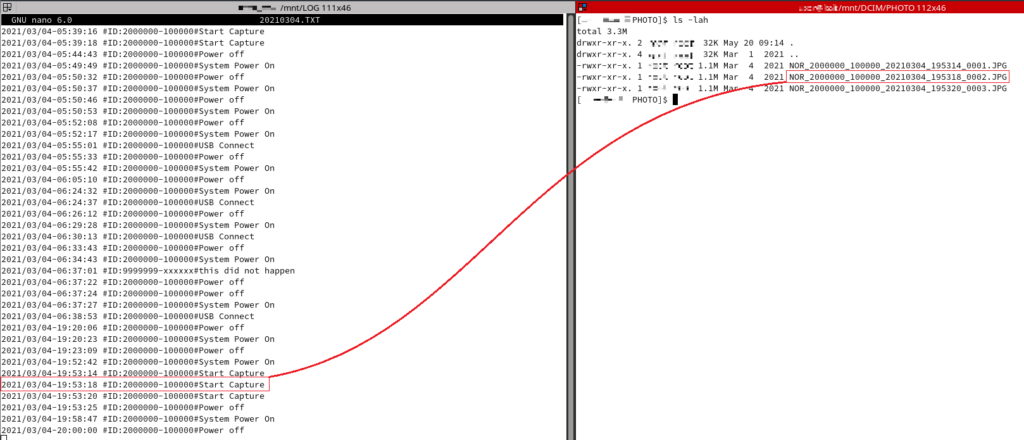
Click for larger
Deleting is pretty straight forward. Referencing the image below:
#1 We delete the file
#2 We remove the log entry
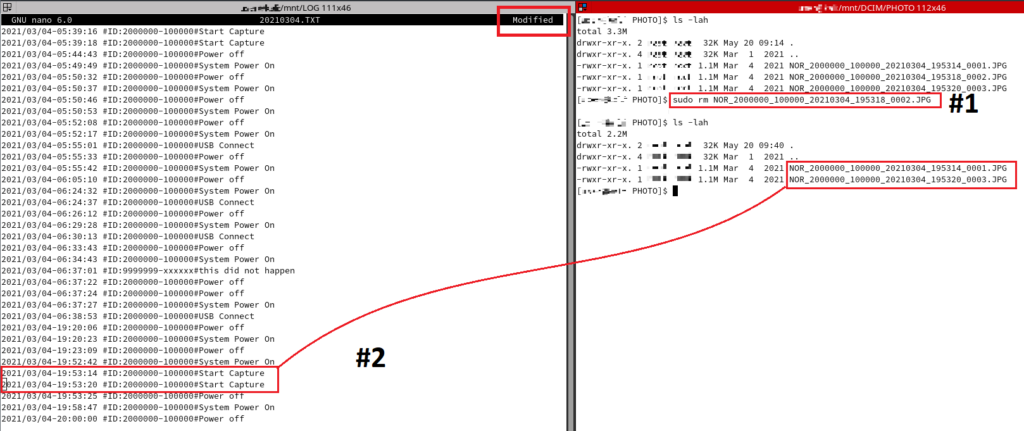
Click for larger
Identified Vulnerabilities
| Vulnerability | CWE | Likelihood | Impact | Risk |
| “Universal” 888888 Password | CWE-798 | High | High | High |
| Potentially sensitive data (video, audio, photos) are not encrypted. | CWE-311 | High | High | High |
| Ability to alter logs | CWE-922 | High | High | High |
| Ability to alter stored video, audio, and photos | CWE-922 | High | High | High |
| Video, audio, and photos stored on removable TF card | CWE-921 | High | High | High |
| Boblov publicizes that there is a “universal” password | CWE-1273 | High | High | High |
Some identified threats that may be able to exploit the above vulnerabilities include:
- Insiders: Those assigned the device which perhaps may have “accidentally” recorded something unflattering and wish their supervisors not to have a chance to review it. The compromise of data integrity and its resulting consequences on an organization could be massive.
- Errors or failures: If the TF card gets lost or somehow falls out, the resulting loss of data availability could not only be catastrophic to a case, but the breach of confidentiality may also be catastrophic from a liability perspective. Though perhaps more reliable than before, TF Cards are still prone to failure.
- External Actors: If the device is stolen, acquired, or otherwise accessed by a malicious third party, the lack of integrity controls and encryption makes it nearly impossible for the owner to know if tampering occurred or if data was accessed/reviewed without authorization.
Summary
The Boblov KJ21 purports to be “…the body camera for law enforcement…” Despite the claim, however, after assessing the Boblov KJ21 and in the context of the high-security control objectives law enforcement has, the Boblov KJ21 was found to have several high-risk vulnerabilities, which would make using this product in a law enforcement setting high risk.
Though this assessment aims to provide information that may help you make a risk-informed decision, there is no substitute for a true risk assessment to consider the particularities of your specific environment and use case, something a general assessment such as this cannot do.

Click for larger
About
Josh Olson has been an explorer since childhood, always the one disassembling gadgets to see how they worked. That inquisitive nature evolved into a passion for cybersecurity, leading him to do, among other things, independent security research and uncovering several Common Vulnerabilities and Exposures (CVEs), particularly in IoT devices. Armed with a Master’s degree in Cybersecurity Information Assurance and a CISSP certification, he’s dedicated to empowering clients and the public with information to make better risk-informed decisions. But Josh isn’t all tech; when he’s not delving into digital mysteries, he enjoys capturing moments through photography and chuckling over stand-up comedy – as an observer rather than a performer, an important distinction he insists we make.
Supplemental
Table1: Security Objectives
| Security Objectives | Low (L) | Moderate (M) | High (H) |
| Confidentiality Preserving authorized restrictions on information access and disclosure, including means for the protection of personal privacy and proprietary information | The unauthorized disclosure of information could be expected to have a limited adverse effect on organizational operations, assets, or individuals. | The unauthorized disclosure of information could be expected to have a serious adverse effect on organizational operations, organizational assets, or individuals. | The unauthorized disclosure of information could be expected to have a severe or catastrophic adverse effect on organizational operations, assets, or individuals. |
| Integrity Guarding against improper information modification or destruction, and includes ensuring information non-repudiation and authenticity | The modification or destruction of information could be expected to have a limited adverse effect on organizational operations, assets, or individuals. | The modification or destruction of information could be expected to seriously affect organizational operations, assets, or individuals. | The modification or destruction of information could be expected to have a severe or catastrophic adverse effect on organizational operations, assets, or individuals. |
| Availability Ensuring timely and reliable access to and use of information | The disruption of access to or use of information or an information system could be expected to have a limited adverse effect on organizational operations, assets, or individuals. | The disruption of access to or use of information or an information system could be expected to seriously affect organizational operations, assets, or individuals. | The disruption of access to or use of information or an information system could be expected to have a severe or catastrophic adverse effect on organizational operations, assets, or individuals. |
Table 2: Boblov KJ21 “Police Body Camera” Information Type
| Information Type | NIST SP 800-60 Reference | Confidentiality L/M/H | Integrity L/M/H | Availability L/M/H |
| Criminal Apprehension | D.16 Law Enforcement | H | H | H |
| Criminal Investigation and Surveillance | D.16 Law Enforcement | H | H | H |
| Executive Functions | C.2.8 General Government | M | H | H |
| Record Retention | C.3.5 Information & Technology Management | M | H | H |
| Overall Rating | M / H | H | H |
Table 3: Impact Definitions
| Magnitude of Impact | Impact Definition |
| High | Exercise of the vulnerability (1) may result in the highly costly loss of major tangible assets or resources; (2) may significantly violate, harm, or impede an organization’s mission, reputation, or interest; or (3) may result in death or serious injury. |
| Moderate | Exercise of the vulnerability (1) may result in the costly loss of tangible assets or resources; (2) may violate, harm, or impede an organization’s mission, reputation, or interest; or (3) may result in injury. |
| Low | Exercise of the vulnerability (1) may result in the loss of some tangible assets or resources; (2) may noticeably affect an organization’s mission, reputation, or interest. |
Table 4: Likelihood Definitions
| Level | Likelihood Definition |
| High | The threat source is highly motivated and sufficiently capable, and controls to prevent the vulnerability from being exercised are ineffective. |
| Moderate | The threat source lacks motivation or capability, or controls are in place to prevent, or at least significantly impede, the vulnerability from being exercised. |
| Low | The threat source lacks motivation or capability, or controls are in place to prevent, or at least significantly impede, the vulnerability from being exercised. |
Table 5: Risk Level Definitions
| Magnitude of Impact | Risk Level Definitions |
| High | There is a strong need for corrective measures. An existing system may continue to operate, but a corrective action plan must be put in place as soon as possible. |
| Moderate | Corrective actions are needed, and a plan must be developed to incorporate these actions within a reasonable period. |
| Low | Some authorizing official must determine whether corrective actions are still required or decide to accept the risk. |
Flashrom Code
Includes/Flashrom.h#define XTXTech_ID 0x0b
#define XTXTech_XT25F32B 0x4016flashrom.c
{
.vendor = "XTX Technology",
.name = "XT25F32B",
.bustype = BUS_SPI,
.manufacture_id = XTXTech_ID,
.model_id = XTXTech_XT25F32B,
.total_size = 4096,
.page_size = 256,
.feature_bits = FEATURE_WRSR_WREN | FEATURE_OTP,
.tested = TEST_OK_PREW,
.probe = PROBE_SPI_RDID,
.probe_timing = TIMING_ZERO,
.block_erasers =
{
{
.eraseblocks = { {4 * 1024, 1024} },
.block_erase = spi_block_erase_20,
}, {
.eraseblocks = { {32 * 1024, 128} },
.block_erase = spi_block_erase_52,
}, {
.eraseblocks = { {64 * 1024, 64} },
.block_erase = spi_block_erase_d8,
}, {
.eraseblocks = { {4 * 1024 * 1024, 1} },
.block_erase = spi_block_erase_60,
}, {
.eraseblocks = { {4 * 1024 * 1024, 1} },
.block_erase = spi_block_erase_c7,
},
},
.printlock = spi_prettyprint_status_register_bp3_srwd,
.unlock = spi_disable_blockprotect_bp3_srwd,
.write = SPI_CHIP_WRITE256,
.read = SPI_CHIP_READ,
.voltage = {2700, 3600}, /* 33F 2.65V..3.6V */
},