
WKL is releasing a new tool focusing on Azure DevOps enumeration with an emphasis on cases where you as an attacker don’t have a username and password to log into the Azure Portal. This tool will retrieve the DevOps data using its API calls.
Azure provides two different types of Authorization values: Bearer token and Basic Auth. So, let’s begin this blog post by first understanding the Azure DevOps Structure.
Az DevOps lies under Entra ID, which used to be called Active Directory. Any user in Entra ID can create DevOps Organization for themselves — even admin/Global Admin cannot stop them from accessing it.
So, let’s first learn the structure of Azure DevOps:
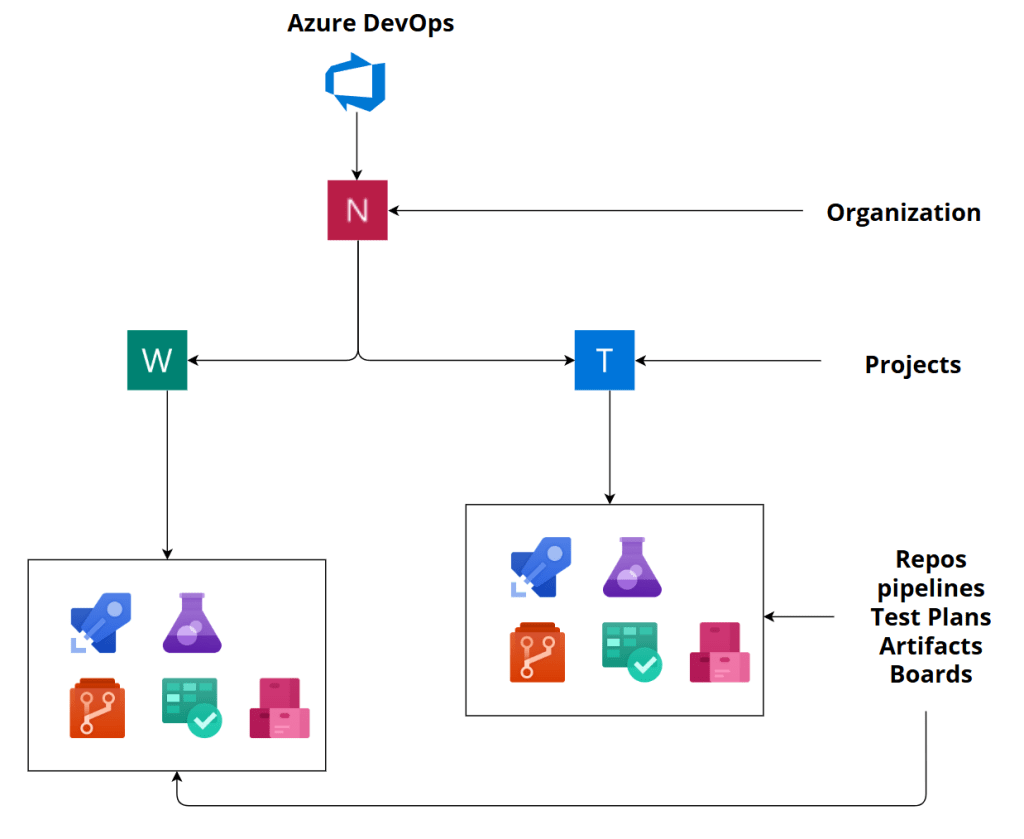
The top layer is the Organization. Any user can have multiple organizations in the Entra ID tenant, under which multiple projects can be created. Below this is the main section where all the repositories are stored. For enterprise companies that use Azure for their Infra setup, most of them heavily use Azure DevOps for CICD Pipelines to help them manage their continuous deployment smoothly.
However, every new feature comes with risk and the possibility of misconfigurations. We won’t we covering the list of possible misconfigurations in Azure DevOps in this blog post.
In DevOps, you might think that only a user can access this, right? But it’s not limited to actual users but is also accessible to service principals including managed identities. This means a VM created in Azure can also access Azure DevOps based on permissions granted to it!
So how can an identity access it? If managed identity is enabled on any compute system like a VM, Logic App, Automation Account, App Service, Function App, etc., their identity gets created within the Entra ID just like the identity exists for a user. This means this identity now can have any kind of role, like Entra ID Roles, access to a subscription, or Azure DevOps.
Let’s quickly check if you have service principal creds that is the Client ID, Client Secret, and Tenant ID. You can run a Azure CLI Command or a PowerShell command to request the token.
az account get-access-token |
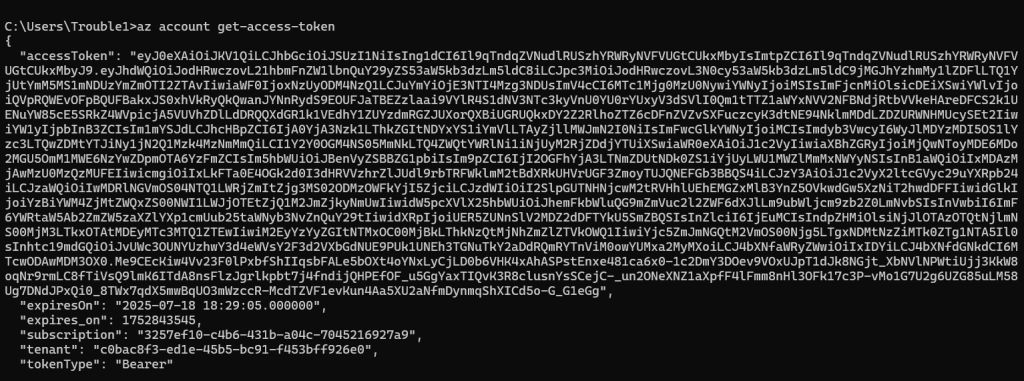
But will this token work? Unfortunately not. Azure requires different tokens for its different resources. These resources can represent different types, such as graph resources for user data or ARM resources for Azure management.
Below are examples with their corresponding endpoints or resource IDs to request access tokens. These URLs are used as endpoints for API calls, specifying the target service for data access or management:
- Microsoft Graph API: https://graph.microsoft.com
- Azure Resource Manager (ARM) API: https://management.azure.com
- Azure Storage REST API: https://storage.azure.com
- Azure Key Vault REST API: https://vault.azure.net
These application IDs (resource IDs) are used in OAuth token requests to specify the particular Azure or Microsoft service being accessed:
- Azure DevOps: 499b84ac-1321-427f-aa17-267ca6975798
- Microsoft Graph: 00000003-0000-0000-c000-000000000000
- Azure Active Directory Graph: 00000002-0000-0000-c000-000000000000
- Azure Resource Manager (ARM): 797f4846-ba00-4fd7-ba43-dac1f8f63013
- Office 365 SharePoint Online: 00000003-0000-0ff1-ce00-000000000000
- Power BI Service: 00000009-0000-0000-c000-000000000000
So, we can provide either the URLs or the IDs depending on which resource API we want to access. Since we are focusing on Azure DevOps, let’s use 499b84ac-1321-427f-aa17-267ca6975798 and grab the token for this.
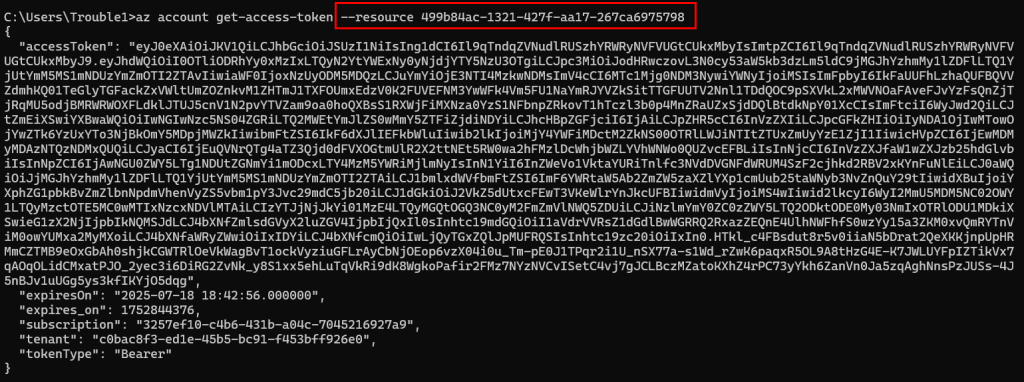
Considering this is clearly a JWT, let’s analyze the token check in jwt.io:
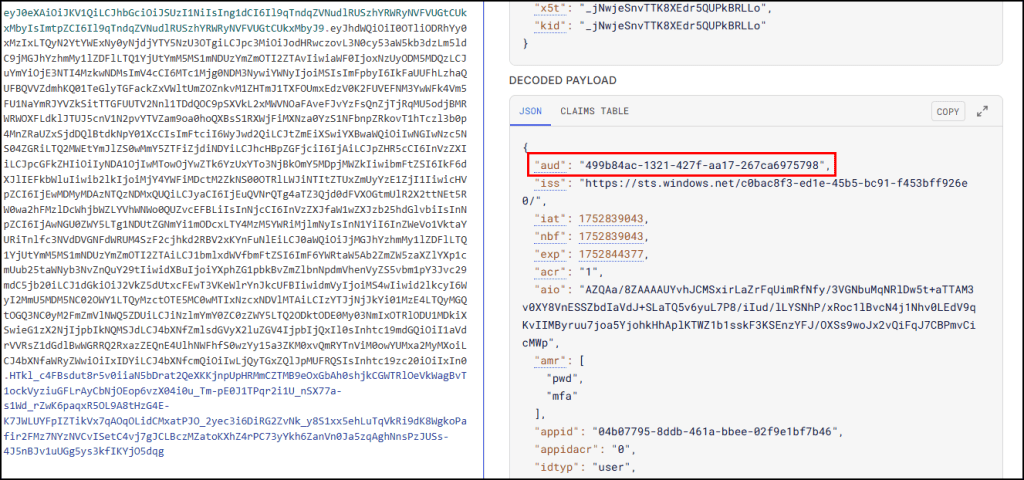
While checking the aud value, we can confirm which resource token are we currently using.
This is where the AzDevRecon comes in, with a UI based tool that allows you to perform the enumeration more efficiently than via CLI.
The application is hosted live, so there is no need to install tooling & troubleshoot dependencies — simply register yourself and get logged in with your account.
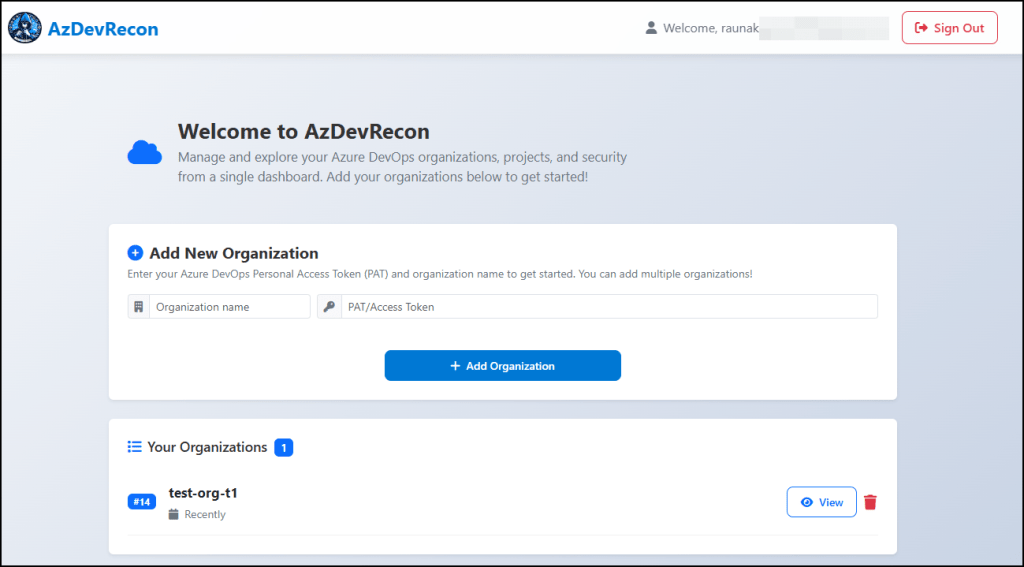
Once logged in, you can start adding the ORG name and the Access Token or the PAT value. For me, I have already added an organization. Just click on the View button to look through the list of projects you have access to.
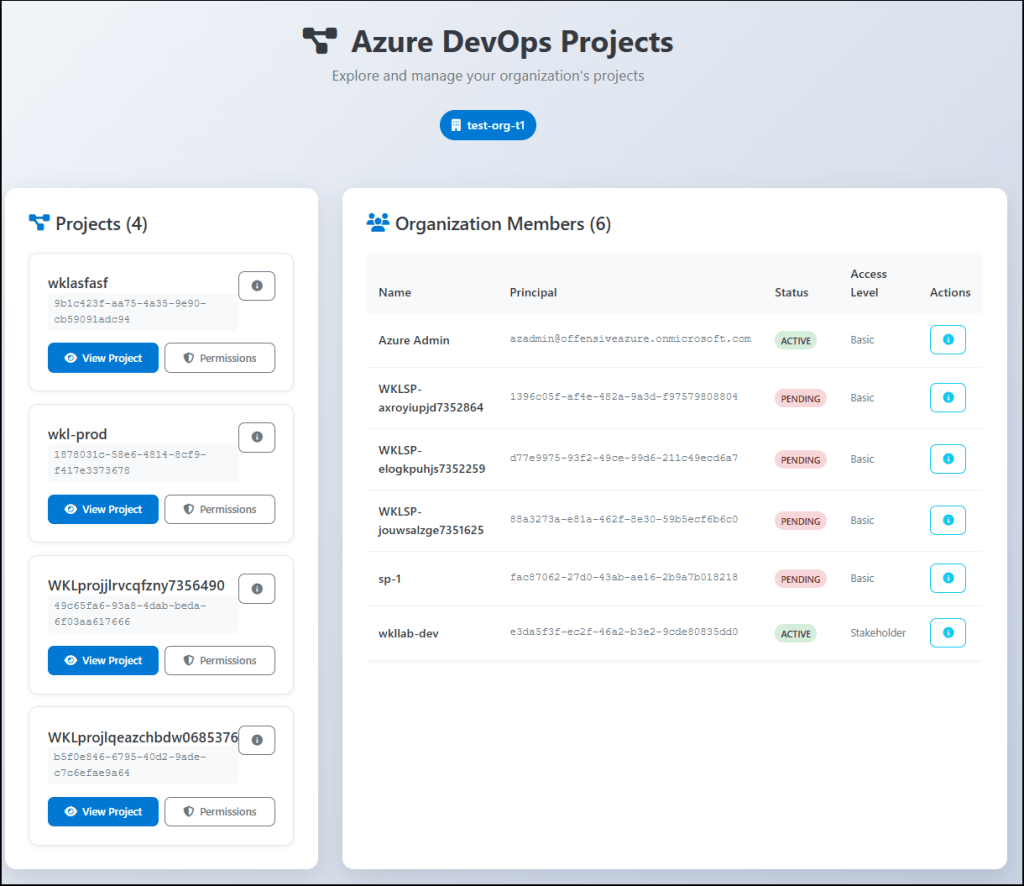
On the left side, we have a list of projects the identity has access to, and the right lists the members available in the organization.
Click any Project (for example, we’ll click “wkl-prod“) to see the dashboard.
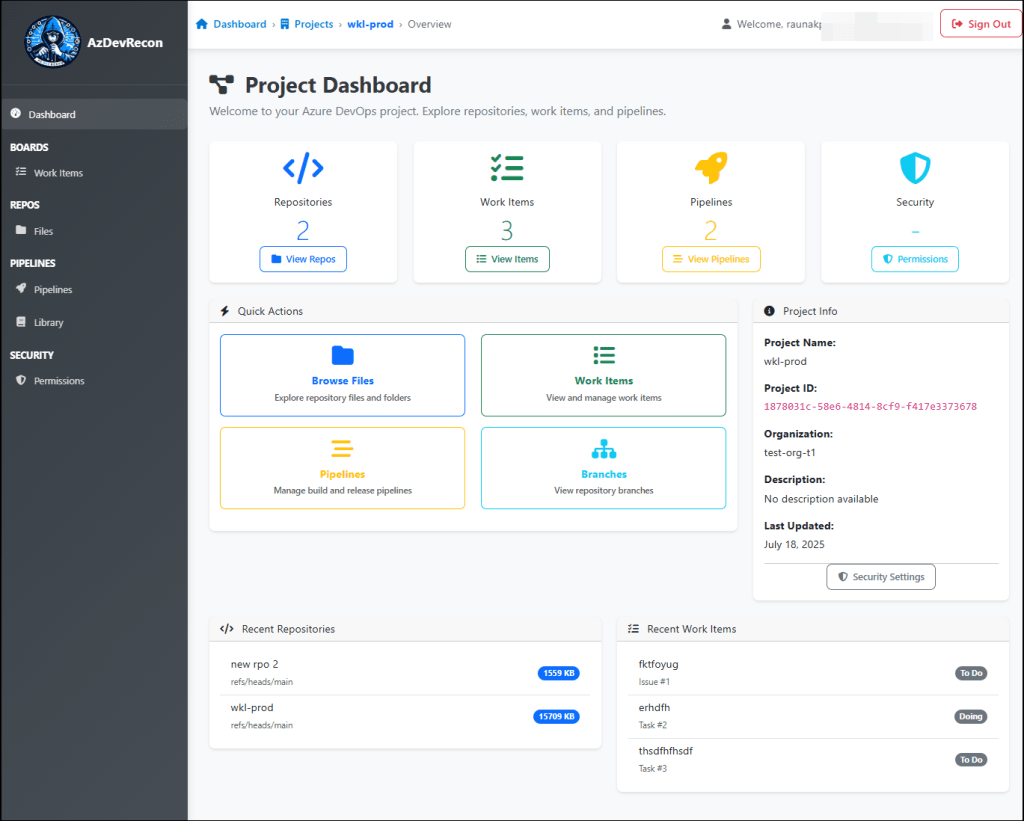
This is our main dashboard where you will be able to see the list of repos, work items, pipelines and the permissions list. So, by clicking on Browse files, a list of repos will display.
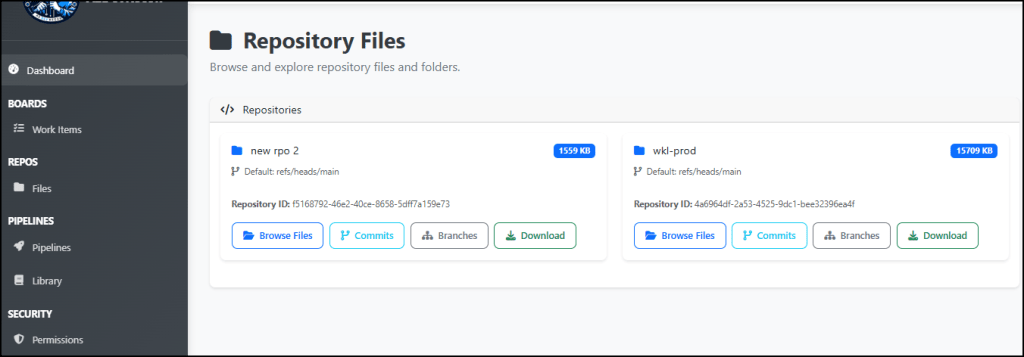
Navigate again to Browse Files.
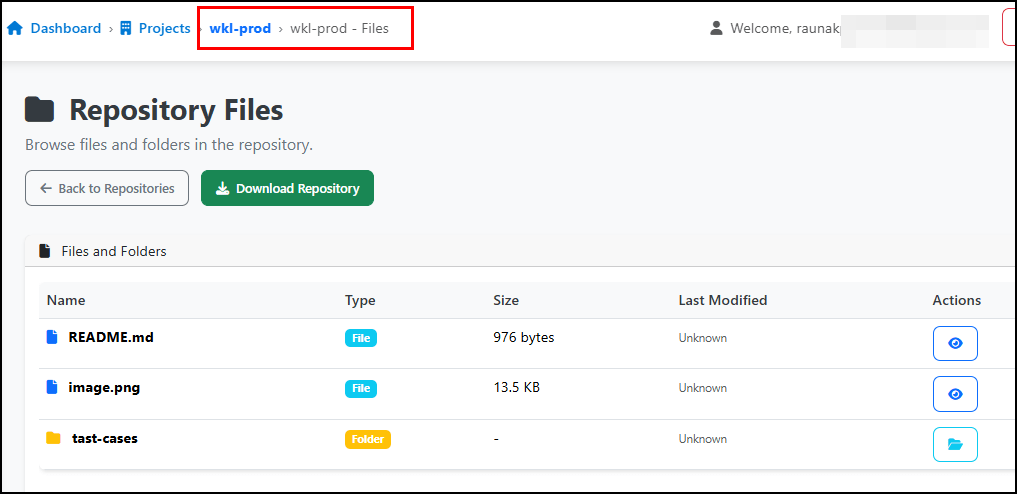
You can even navigate to each folder and try to edit the files as well. Just click on the eye icon.
Then click the Edit button and a new popup will display like in the screenshot below.
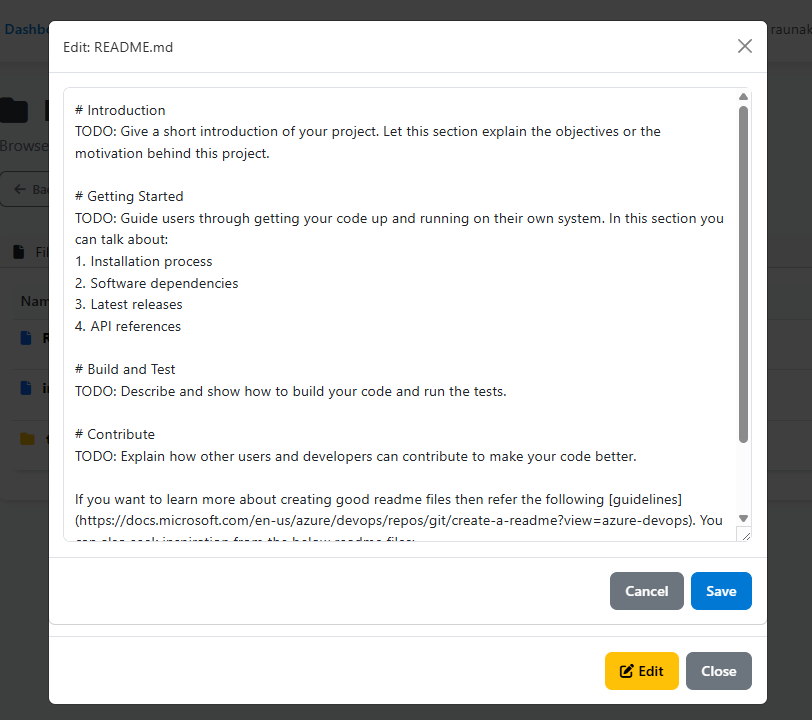
Now we can make changes, but note if your PAT or Access Token doesn’t have the permission, you will trigger a permission alert. So, for now, we’ll update the first line from # Introduction to # The Demo.
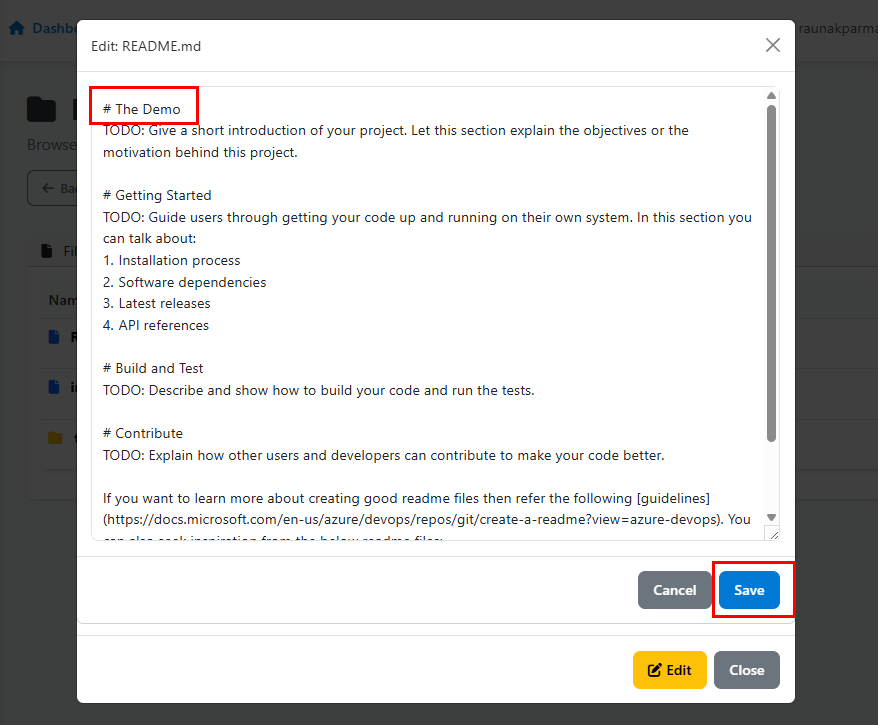
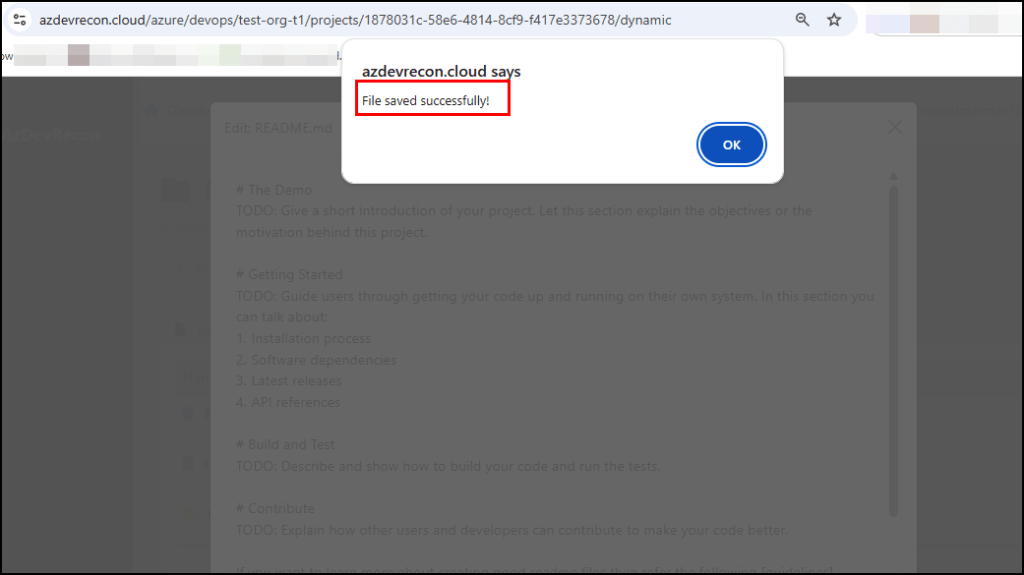
Once you click on Save, you should see an alert box like in the image below, or permission error if you don’t have the permission to edit.
You can even download the whole repo using the Download Repository button. The images below show other routes to view the data.
Pipelines List and its YAML File
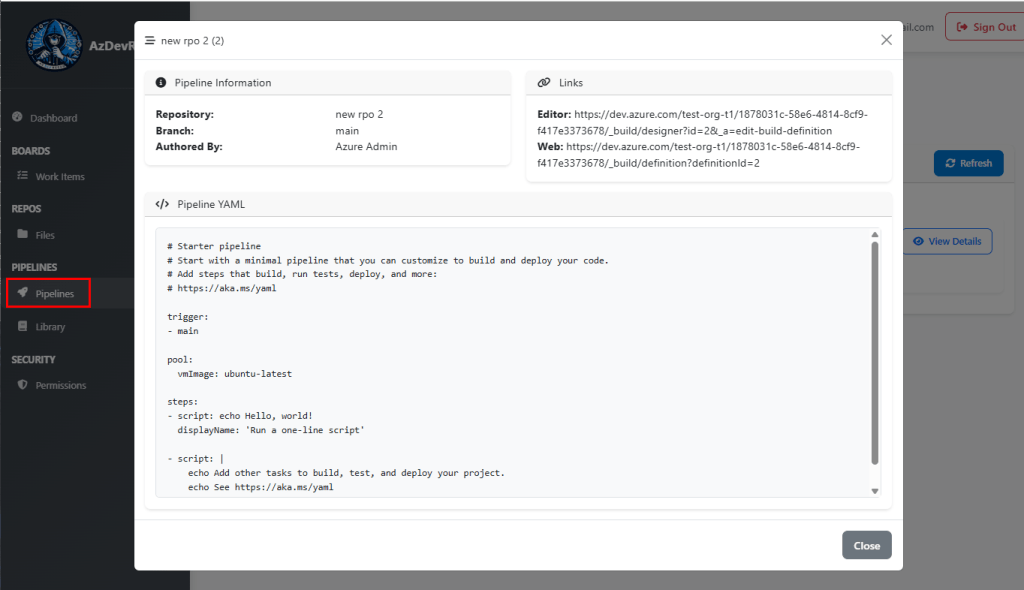
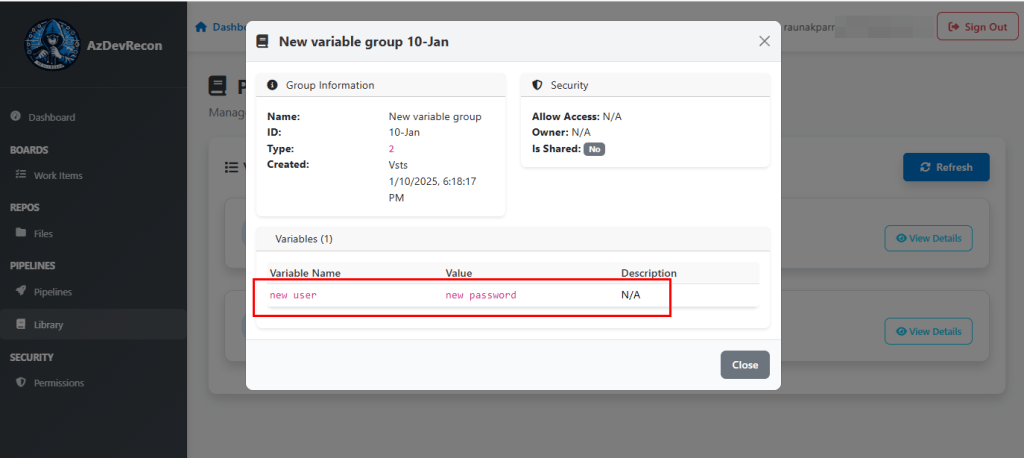
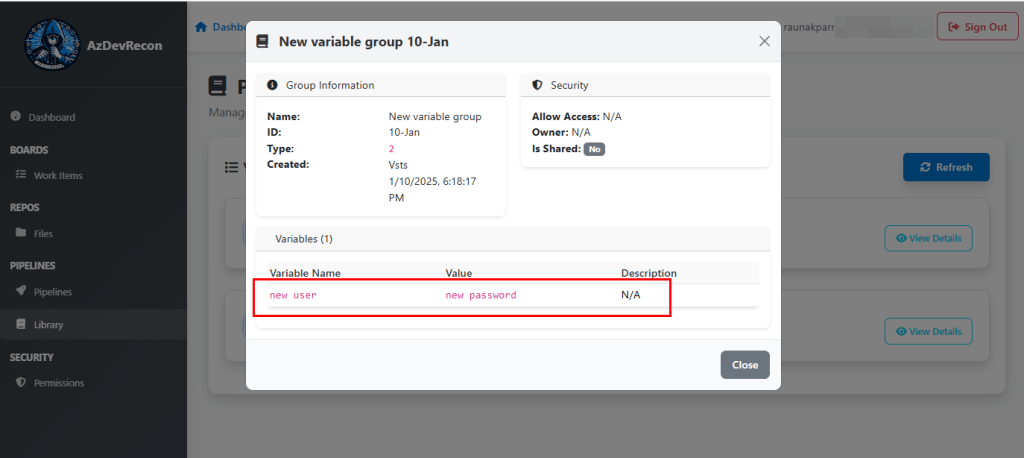
Pipeline Variables
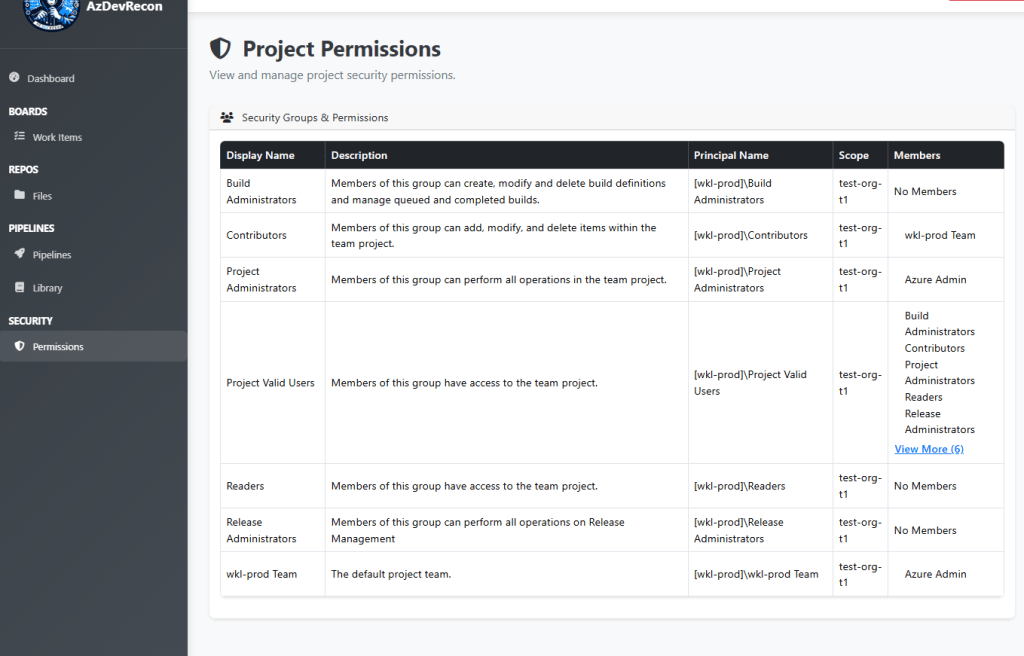
Project Permissions
Work Items
The tool is certainly not limited to what’s shown here. Since it’s an early release, you can expect a lot more features, which can make your enumeration job easier—like a list of all repos all in one place, better permissions mapping visual, a list of all the Project setting, the ability to perform malicious activity, which can allow you to have a backdoor/persistence in it, etc.
I have created a discord channel for those who would like to contribute to this project or want to give any feedback or recommendations. We can work together to make this tool more powerful.
Posted by:
Senior Cloud Security Engineer


